Think SOC 2 is a boring compliance topic? Think again. If you’re a SaaS startup, this designation gives you a competitive edge. Background checks are a key enabler of SOC compliance because they help you meet the security controls needed to earn a clean report.
What Is SOC 2 Compliance?
The System and Organization Control (SOC) certification program is a voluntary compliance standard developed by the American Institute of Certified Public Accountants (AICPA).
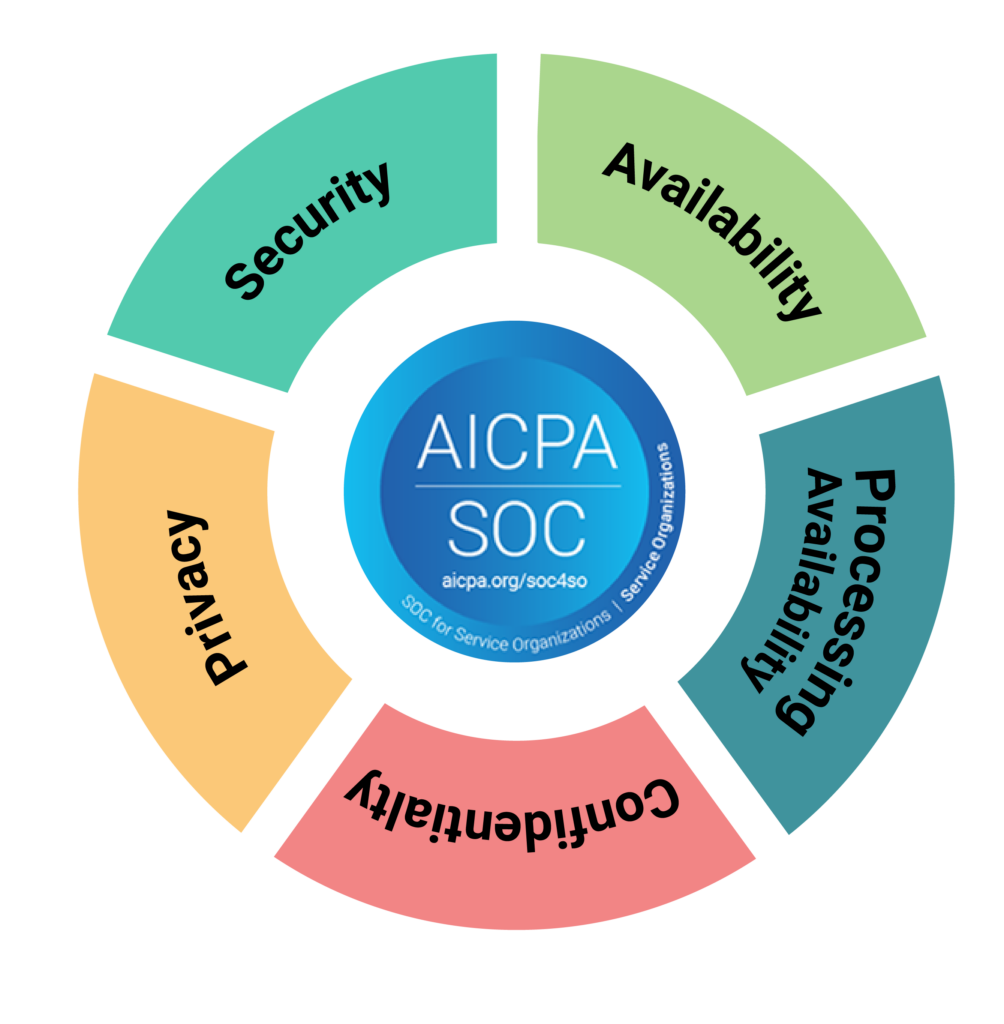
The auditing framework is rooted in five trust principles: security, privacy, confidentiality, processing integrity, and availability. On account of the enhanced internal controls needed to obtain your clean audit report, this designation confirms your business has stringent processes in place to securely manage its data.
This certification is rapidly becoming one of the top security standards vendors, clients, and customers all look for, so you could be missing out on business without it. Learn more about the different types of SOC compliance.
Who’s Required to Be SOC 2 Compliant?
If you’re a service provider or your organization generally stores customers’ data in the cloud, this type of compliance report is applicable to your business.
While not mandatory, for many companies a clean report is a key requirement when considering which third-party vendor to hire. The contractual commitments in your service level agreements may indicate which controls you should put in place or should look for in others.
New services with outsourcing arrangements that drive adoption include:
- Software as a service (SaaS)
- Infrastructure as a service (IaaS)
- Platform as a service (PaaS)
- Cloud providers
At Certn, we can assist you with designing a background check program that can help you satisfy the background check requirements needed to earn your SOC 2 certification.
Benefits of SOC 2
Demonstrating this kind of commitment to information security has obvious benefits for any company that stores its data in the cloud because mishandled data can leave businesses vulnerable. More than that, it helps a brand stand out as a privacy leader. It signals to clients and customers that your business processes consistently exceed regulatory requirements. In fact, some companies will only do business with partners and vendors that are certified. For example, for your company to remain compliant, all your third-party vendors must be compliant too. Without it, you may lose out on business.
Aside from distinguishing your brand as trustworthy and enhancing your reputation, the security controls protect your business from cyber attacks and data breaches.
The Cost of a Data Breach
The financial costs associated with data breaches can be significant. A company may have to pay for damages, upgrades or replacements of compromised systems, legal fees, and/or credit monitoring services for any affected customers. Data breaches also carry risks beyond financial losses. In some cases, there may also be reputational damage that affects the future success of the business.
As we’ve covered in another compliance-related blog post, you open yourself up to potential risks when you don’t have the right processes in place to protect your business.
Data breaches are a serious and growing problem for companies of all sizes. According to IBM’s The Cost of a Data Breach Report 2022, 83% of companies will experience a data breach at least once.
Ultimately, the price tag on a data breach cannot be underestimated – both in terms of money and reputation. Taking the right steps to prevent a data breach is essential for any business that wants to avoid costly repercussions. Having a strong compliance program in place can help ensure your company’s security – while also giving you peace of mind.
Average Cost of Data Breach
The IBM report goes on to add that data breaches cost companies $4.35M on average, and that the industry with the highest average data breach cost is healthcare at $10.10M.
The average cost of a data breach is also significantly higher in North America than in the rest of the world, with companies in this region facing an average of $5.51M compared to $3.86M globally. This is due to increased regulatory costs and legal action that can occur after a data breach occurs.
Data Security for Businesses
It’s important for companies of all sizes to invest in security to protect themselves from cyber risk. Data by researchers at the cloud security company Barracuda Networks revealed that small businesses are three times more likely to be targeted by cybercriminals.
Data security is especially important for businesses, as it safeguards their sensitive data and customer information. It’s essential to establish policies and procedures to protect that data, such as encrypting it in transit or at rest, having a secure network infrastructure with firewalls, and ensuring only authorized personnel have access to the data.
Businesses should also create a comprehensive backup plan in case of a serious breach or malicious attack. This should include regularly backing up all important data in multiple locations so that if something is lost or stolen, you can easily recover it without losing valuable time or money. Additionally, companies should consider investing in cyber insurance coverage to help bear the cost of expensive recovery efforts after a cyber attack.
Finally, training employees on cyber-security best practices is essential. All members of an organization should be aware of the risks associated with data security and know how to protect their company’s data from being compromised. This includes educating them on topics such as phishing, password hygiene, and social engineering.
By investing in data security measures and educating employees about cyber-security best practices, businesses can reduce the risk of becoming a victim to online threats. With the right security measures in place, companies can protect their valuable assets and ensure sensitive customer information remains safe.
Root Causes of Data Breaches
According to 2022 IBM data, these are some of the root causes of data breaches:
- 19% Stolen or compromised credentials
- 16% Phishing
- 15% Cloud misconfiguration
- 13% Vulnerability in third-party software
- 9% Physical security compromise, responsible for of breaches
- 8% Malicious insider
To address some of the most common causes of data breaches described above, approaches need to be holistic.
This is why SOC 2 compliance has become the gold standard for data security: Its comprehensive and principle-based approach is designed to meet the individual needs of any company, no matter its size or industry.
SOC 2 Background Check Requirements
Background checks are generally regarded as the best practice for meeting the integrity and ethical values requirement (CC1.1) under the security principle. Why? Background checks demonstrate evidence of a standard screening process and due diligence when hiring new employees. What the requirements don’t cite are the particular requirements of the background check, which means you have the flexibility to adopt whatever process works best for you.
The five trust service criteria (TSC) that make up SOC 2 are: security, privacy, confidentiality, processing integrity, and availability.
Security, which includes things that protect data systems from unauthorized access, is the only TSC that must be included. It’s the baseline with nine common criteria you must develop controls for, whereas the others can be included at the discretion of your management. You only need to adopt a control if it applies to you.
On top of this, automating as much as possible is a best practice. A background check provider with an open background check API that’s easy to integrate into your hiring processes and platform provides an added advantage.
SOC 2 Background Check Compliance
Background screening is an important security step to ensure only trustworthy and qualified employees are hired. It’s also one of the controls that you need to implement for passing your SOC 2 audit. Background screening ensures due diligence is done for employees who have access to sensitive information and privileged accounts within your organization and reduces the risks of insider threats.
Performing background checks allows obtaining evidence of security checks like:
- Identity verification;
- Checking that they have the experience and qualifications that they claim;
- Ensuring that they’re not a security risk to your company; and
- Verifying that they’re legally allowed to work at your company.
Identity Verification
Over the last few years, the Society for Human Resource Management (SHRM) has reported on the rise of applicant fraud.
Ultimately, identity verification is an important step in the recruitment and onboarding process. In today’s digital age, it’s increasingly important for employers to verify not only the authenticity of a candidate’s information but also their identities to protect the organization from applicant fraud. By instituting an identity verification protocol prior to on-boarding new hires, companies can improve security and reduce risk associated with hiring decisions.
Can You Hire Someone With a Criminal Record and Maintain SOC 2 Compliance?
It’s possible to maintain SOC 2 compliance while hiring candidates who have a criminal record. Here’s why: conducting background checks when hiring is about demonstrating due diligence, not about excluding a specific population from your talent pool.
By conducting background checks, you demonstrate that you have controls in place, are upholding a standard process, and are making informed hiring decisions when bringing on new employees.
When evaluating candidates with a criminal record, you can look for green flags that they’re trustworthy, such as:
- The amount of time elapsed since the offence;
- The offence is unrelated to the job;
- If they’ve done similar work in the past without incident; and/or
- The nature and gravity of the offence.
You can discuss the matter with your legal counsel to align your hiring policies (like a fair chance hiring program) with your established security procedures. Ultimately, you want to hire the most qualified candidate for the job. By taking these extra steps and conducting meaningful background checks, you can maintain your standards and still bring on great people who may have made mistakes in their past.
How to Protect Your Business
A compliant cybersecurity program and clean audit gives you a competitive edge. SOC 2 signals to clients and customers that your business processes consistently exceed regulatory requirements, and background checks help ensure that employees with access to sensitive information and privileged accounts won’t compromise your data or your reputation.
Certn is a SOC 2-certified background check provider that’s trusted by over 10,000 clients. Book a demo today to learn more about how you can work toward achieving this designation.
Legal disclaimer: The information contained in this blog post is for general informational purposes only and does not constitute legal advice.





