Developed by the Association of International Certified Professional Accountants (AICPA), Service Organization Control (SOC) 2 is an auditing procedure that verifies companies have internal controls in place to protect sensitive data, and that the controls are operating continuously.
Released in 2010, it quickly became a standard for software as a service (SaaS) companies and managed service providers. SOC 2 is voluntary, so not all companies need to be compliant to operate, but if you deal with data and store data in the cloud, earning a clean audit can improve your ability to sign new clients and get ahead of the competition.
Below we break down the different designations and the benefits of becoming compliant if you aren’t already. Of course, we also cover how background checks help achieve SOC 2 compliance.
SOC 1 vs SOC 2
SOC 2 implies the existence of others, of which there are several. In total, there are actually three: SOC 1, SOC 2, and SOC 3 — all simultaneously released in 2010 by the AICPA.
It’s worth noting that they were all developed and released at the same time because it can be easy to assume that SOC 2 is an evolution of #1, or that SOC 3 is an upgraded and more comprehensive version of the second one. But that’s not the case. Rather, each type covers something a little different.
This means that you don’t need to get #1 before getting #2, or that #3 provides more benefits than #2.
Different Types of SOC
The table below outlines the different types:
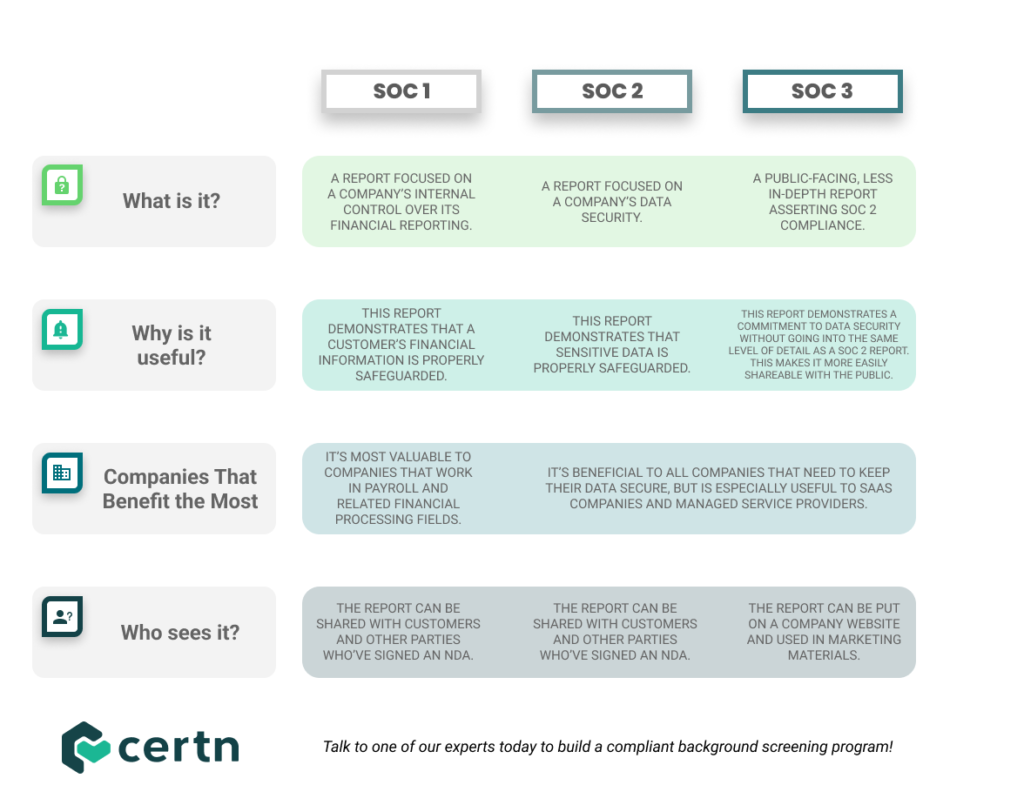
SOC Compliance Types
Within SOC 2 (and SOC 1), there are two subtypes: Type 1 and Type 2.
SOC 2 Type 1
This type examines whether your company met the requirements for SOC 2 compliance on a specific date, it’s a snapshot in time.
Due its short time span and smaller scope, Type 1 can be useful when working under a tight deadline. However, because it’s less comprehensive, clients may not be as interested in seeing it. They’ll likely be looking for a report that demonstrates continuous compliance over a longer period of time.
SOC 2 Type 2
This type determines whether a company has maintained continuous SOC 2 compliance over a long period of time, rather than at a specific point in time.
Typically, Type 2 reports cover several months to a year. The time frame they cover can’t exceed a year, though, which means that for a company to remain compliant, it must regularly undergo audits. When people talk about SOC 2 compliance, this is typically the subtype they’re referring to or are looking for.
SOC 2 Compliance Checklist
Is there a checklist? No, not exactly.
Because the needs of a company depend on a number of factors, including its size, customer base, industry, and processes, achieving a clean audit isn’t about meeting a standard checklist. Rather, it’s about demonstrating that you’ve implemented custom processes necessary to maintain your specific company’s security standards, and having their effectiveness and rigor validated by an outside auditor.
To achieve this level of compliance, your custom policies must be rooted in the five Trust Service Criteria:
- Security
- Privacy
- Confidentiality
- Processing Integrity
- Availability
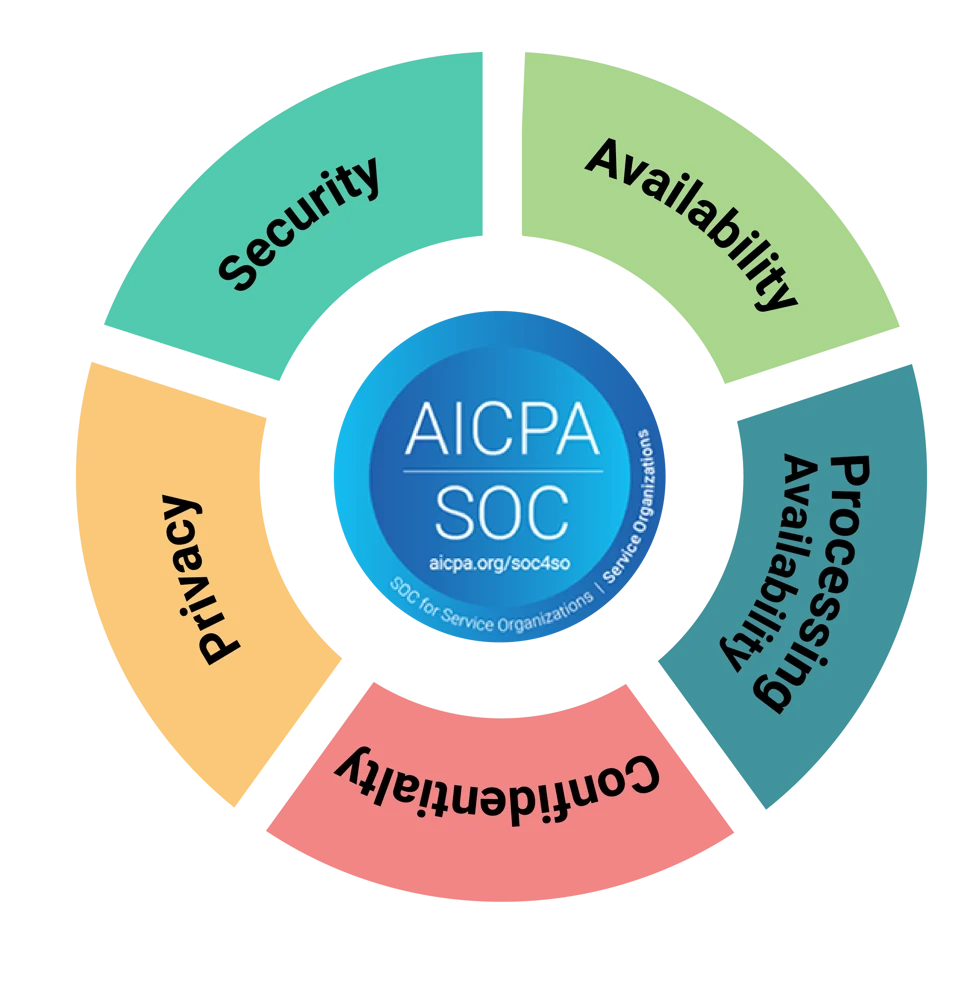
As we outlined in this blog post that describes how background checks help SOC 2 compliance, the security principle is a mandatory TSC, whereas controls for the principles can be included at the discretion of your management. You only need to adopt controls that apply to your business.
Benefits of SOC 2 Compliance
This kind of commitment to information security has benefits to many companies because mismanaged data can leave businesses vulnerable to growing cyber attacks and data breaches. Aside from distinguishing your brand as trustworthy and enhancing your reputation, the security controls protect your business from cyber attacks and data breaches.

Third-Party Risk Management
According to a Splunk Global Research survey of over 1,200 global security leaders, 90% of organizations reported that they’ve increased their focus on third-party risk assessment as a result of recent cyber attacks.

SOC 2 Competitive Advantage
SOC 2 is as recognized as ISO 27001 is in North America. In fact, some companies, especially in the United States, will only do business with partners and vendors that are certified to prove they’ve implemented security controls to protect customer data. Without it, you might miss out on revenue.
Other businesses that rely on outsourcing arrangements are also driving adoption:
- Software as a service (SaaS)
- Infrastructure as a service (IaaS)
- Platform as a service (PaaS)
- Managed service providers
By nature, early-stage startups have smaller security teams, so having SOC can set you apart as a trustworthy partner.
Uphold Cybersecurity Regulations
Regulated industries that are undergoing a major flux due to technological innovation like health care, financial services, and education are likely to benefit from certification because it gives investors, partners, vendors, and customers extra assurance. It’s the same way that background checks give you extra peace of mind.
SOC 2 Compliance Automation – The Certn Difference
Compiling the documentation you need and putting in place continuous IT vendor monitoring can be daunting. Fortunately, there are leading information security platforms designed to make the process as easy as possible. Even better? Certn’s background checks API means we integrate with many of them.
We’ve partnered with industry leaders to integrate background checks into their platforms, making it easier to keep track of all your compliance efforts. One of our partners, Drata, offers a compliance solution that features automated monitoring and evidence collection that alert you of any failed controls (like incomplete background checks) to keep you audit-ready at all times.
If you’re ready to get started on the background checks required to achieve SOC 2 compliance, book a demo to learn more about how Certn and our partners can help.






